How To Manually Set Up A Custom / Vanity Domain Name In Windows Server Essentials
Let me start off by saying that I typically recommend folks use a Microsoft personalized domain name (e.g. YourDomainPrefix.remotewebaccess.com) when setting up Anywhere Access / Remote Web Access on their Essentials server. The reason for this is that the domain name, the dynamic DNS update service, and the trusted SSL certificate are all automatically set up and managed for you by the Essentials server completely free of any charge or hassle. If you would rather take this much more convenient route instead, then see the following links for instructions on how to set up a Microsoft personalized domain name on your Essentials server:
Configuring and Customizing Remote Web Access on Windows Server 2012 R2 Essentials
Understand Microsoft personalized domain names
EDIT (11/15/2022): With the increased frequency that Microsoft keeps breaking their online services in Windows Server Essentials (including their remotewebaccess.com personalized domain names and dynamic DNS service), it’s becoming abundantly clear that they no longer care about Windows Server Essentials. Therefore, I now STRONGLY recommend that folks avoid using a Microsoft personalized domain name and just set up their very own custom / vanity domain name instead.
That being said, I also understand that some folks would rather forgo the convenience of using a Microsoft personalized domain name in order to have their very own custom / vanity domain name instead (e.g. YourDomainPrefix.YourCustomDomain.com). Using a custom / vanity domain name presents some additional challenges that must be overcome though; such as purchasing, setting up, and managing the domain name, the dynamic DNS update service, and the trusted SSL certificate. For those folks who are willing to take on those additional challenges, I’ll do my best to try and help by walking you through the entire manual domain name set up process here step-by-step (using either a user-purchased SSL certificate or a free Let’s Encrypt SSL certificate via Certify the web).
Set Up Port Forwarding On Your Network Router
The very first thing that you will need to do is make sure that HTTPS port 443 is being forwarded to the private (LAN) IP address of your Essentials server in your network router settings. When you configure your Essentials server for Remote Web Access, the Anywhere Access / Remote Web Access set up wizard attempts to automatically configure your network router settings for you using Universal Plug and Play (UPnP) commands. If your network router doesn’t support UPnP, or if you have turned UPnP off for your router, then you must manually configure your router settings to forward HTTPS port 443 to the private (LAN) IP address of your Essentials server. For information on how to set up port forwarding on your network router go here.
NOTE: Some routers may not work properly with the UPnP port forwarding feature of the Anywhere Access / Remote Web Access set up wizard. Visit the support website for your router manufacturer and ensure that your router has the most recent firmware if you run into any problems. For additional help try here.
NOTE: If you are manually forwarding HTTPS port 443 in your router settings (as opposed to allowing UPnP to do it for you), then you will also need to make sure that you’ve made your Essentials server’s private (LAN) IP address static (so that it doesn’t automatically change and disrupt the port forwarding). For information on how to assign a static IP address go here or here. Alternatively, you can create a DHCP address reservation for your Essentials server in your network router’s DHCP server (or other DHCP server on your network) such that your server always receives the same IP address every time.
NOTE: If you will be using a free Let’s Encrypt SSL certificate (discussed below), and will be validating your domain over HTTP in Certify the web, then you will also need to make sure that HTTP port 80 is being forwarded in your router settings as well. Otherwise, it isn’t really needed.
Purchase A Custom / Vanity Domain Name
Next, you will need to purchase a custom / vanity domain name (e.g. YourCustomDomain.com) from a domain registrar if you don’t already have one. There are many domain registrars to choose from. I’ll be using GoDaddy in a few of my examples below, but with all of their silly antics, I STRONGLY suggest that you avoid them and choose a different domain registrar instead (such as Namecheap, etc.). Also, a few things that you may want to take into consideration when choosing your domain registrar are:
• If your Internet Service Provider (ISP) only offers a dynamic IP address (as opposed to a static one), which is common, then you will need to use a dynamic DNS update service (discussed below) in order to ensure that your domain name is always properly pointed to the ever-changing public (WAN) IP address of your network router (i.e. so that your domain name’s public DNS records are always kept updated with the current IP address that is being issued to your network router by your ISP – via your cable modem, etc.). Therefore, you may want to choose a domain registrar that provides a free dynamic DNS update service for their hosted domain names.
• If you want to use a free Let’s Encrypt SSL certificate (discussed below), and you can’t validate your domain over HTTP seeing as your ISP is blocking HTTP port 80, or because you want to use a wildcard SSL certificate, then you may want to choose a domain registrar that offers a free DNS service, which allows you to fully manage all of your domain’s DNS settings, so that one of the supported DNS API providers can be used to validate your domain via DNS in Certify the web.
• You may want to choose a domain registrar that offers a privacy proxy service that can be added to your domain name so that your personal information (email address, street address, phone number, etc.) isn’t made available to the general public when doing a “whois” lookup on your domain name.
NOTE: Namecheap offers fair domain name pricing, a free dynamic DNS service and update client, as well as a free domain privacy service with every new domain registration and transfer. To purchase a new custom / vanity domain name from Namecheap go here.
NOTE: If you are a small business user (instead of a simple home office user), then none of these issues may be of a concern for you since your ISP may be providing you with an unblocked static IP address (so that you can freely use HTTP port 80, and don’t need to use a dynamic DNS update service), and since you may not mind your business information being attached to the public “whois” record of your domain name.
Set Up A Dynamic DNS Update Service On Your Domain Name
Once your custom / vanity domain name has been acquired, and if your ISP provides you with a dynamic IP address, then you will need to set up a dynamic DNS update service for it. Otherwise, if your ISP provides you with a static IP address, then go ahead and skip to the next section of this tutorial now.
If your domain registrar offers a dynamic DNS update service (and update client), then go ahead and follow their instructions in order to set it up for your domain name at this time.
INFO: If your domain registrar doesn’t offer a dynamic DNS update service, or if they charge to use their service, then you may want to consider using Namecheap’s FreeDNS service. It’s fairly easy to set up your existing domain name to use their free DNS service by simply changing your nameserver settings at your current domain registrar as described here. This method is preferable to using the Duck DNS method (mentioned below) seeing as it will keep your root (base) domain (e.g. YourCustomDomain.com) in sync with your ISP’s dynamic IP address, as opposed to keeping only the chosen subdomain of your base top level domain (TLD) in sync (such as remote.YourCustomDomain.com). Unfortunately, unlike the Duck DNS update client, their update client doesn’t run as a scheduled task, or as a Windows service, and so it needs to be continuously running from a Windows desktop in order to be able to perform the dynamic DNS updates, which is a bit of a let down. To resolve this issue, I’ve modified the “Enable-DuckDns” Windows PowerShell update client so that it will work with FreeDNS (BasicDNS or PremiumDNS). You can download the “Enable-FreeDns.ps1” PowerShell script from here. To use the script, you will first need to turn on Dynamic DNS in FreeDNS as described here (making note of your Dynamic DNS Password), create an ‘A+Dynamic DNS Record‘ for the hostname as described here, and then install the PowerShell update client on your Essentials server via the “Windows PowerShell ISE” program (using @ as the host, YourCustomDomain.com as the domain, YourDynamicDNSPassword as the password, and 15 minutes as the update interval when prompted). Doing this will install two scheduled tasks on your Essentials server that will keep your root (base) domain in sync with your ISP’s dynamic IP address.
Otherwise, you can use the free dynamic DNS update service offered by Duck DNS as follows:
1. Register a free account with Duck DNS. You will be assigned a Duck DNS token, and you can easily create a Duck DNS domain to match your existing domain name (e.g. YourCustomDomain.duckdns.org).
NOTE: The Duck DNS website is a bit of an odd duck in that it asks you to sign in using another account such as Twitter, Google, etc. (i.e. they don’t host their own sign in accounts). No big deal, just go ahead and sign in with the account of your choice.
2. Install a Duck DNS update client on your Essentials server in order to keep your Duck DNS domain in sync with your ISP’s dynamic IP address.
NOTE: Duck DNS offers a lot of update clients to choose from. Personally, I’d go with the “Enable-DuckDns” Windows PowerShell update client by Brian Childs seeing as it is well written and works nicely with the Essentials server. To do so, simply download the “Enable-DuckDns.ps1” PowerShell script from its GitHub repository here, then start a Remote Desktop Connection to your Essentials server, sign in as an administrator, run* the “Windows PowerShell ISE” program, File → Open the downloaded script file, File → Run the opened script file, and then enter in your Duck DNS domain (without the trailing “.duckdns.org” – e.g. YourCustomDomain), your Duck DNS token (which you received when you first created your Duck DNS account), and the update interval (in minutes) when prompted. Doing this will install two scheduled tasks on your Essentials server that will keep your Duck DNS domain in sync with your ISP’s dynamic IP address.
*NOTE: Be sure that you right-click Windows PowerShell ISE and select “Run as administrator“.
3. Lastly, you will need to add a ‘CNAME’ record for your chosen subdomain, via the DNS manager at your domain registrar or DNS provider, that points to your Duck DNS domain (e.g. YourCustomDomain.duckdns.org). Further details are provided in the next section of this tutorial.
Set Up The Domain Name Prefix For Anywhere Access / Remote Web Access
You must also choose a domain name prefix (subdomain) for your domain name to use with the Essentials server’s Anywhere Access / Remote Web Access feature (i.e. the YourDomainPrefix portion of your YourDomainPrefix.YourCustomDomain.com custom / vanity domain name). It is recommended that you use “remote” as the prefix for your fully qualified domain name (e.g. remote.YourCustomDomain.com), but feel free to chose a different prefix if so desired.
NOTE: You will be asked for this domain prefix by the Essentials server’s Anywhere Access / Remote Web Access set up wizard in the next section of this tutorial.
Once you’ve chosen a domain name prefix to use, you will then need to add a public DNS record for it using the DNS manager that is provided by your domain registrar or DNS provider. If your ISP provides you with a static IP address, then go ahead and add a new ‘A’ record named “remote” (or whatever prefix you decided on) that points to your static IP address and then move on to the next section of this tutorial now.
Otherwise, if your ISP provides you with a dynamic IP address, then go ahead and add a new ‘CNAME’ record named “remote” (or whatever prefix you decided on) that points to your domain’s primary ‘A’ record (typically this is done by specifying an @ symbol, or your domain name, for the ‘CNAME’ record’s value). You will then need to use your domain registrar’s dynamic DNS update service and update client to keep your domain’s primary ‘A’ record (or ‘A+Dynamic DNS Record‘) in sync with your ISP’s dynamic IP address as mentioned above. Examples of working with ‘A’ and ‘CNAME’ records in GoDaddy are shown here and here.
INFO: Doing this will ensure that the URL https://YourDomainPrefix.YourCustomDomain.com/remote will always take you to your Essentials server’s secure Remote Web Access website, and won’t interfear with any other subdomains that you may be using (such as https://www.YourCustomDomain.com, etc.).
If you are using Duck DNS, then you will need to add a new ‘CNAME’ record named “remote” (or whatever prefix you decided on) that points to your Duck DNS domain name (e.g. YourCustomDomain.duckdns.org). Doing this will keep your fully qualified domain name (such as remote.YourCustomDomain.com) in sync with your Duck DNS domain, which is always pointed to your ISP’s dynamic IP address as mentioned above.
INFO: Duck DNS will only work with a ‘CNAME’ record for a subdomain of your base top level domain (TLD) such as remote.YourCustomDomain.com. It will not work with the primary ‘A’ record for your root (base) top level domain itself (e.g. YourCustomDomain.com).
Set Up A Trusted SSL Certificate For Your Domain Name
Once your domain name is ready to go*, you will then need to purchase a trusted SSL certificate** for it in order to be able to successfully (and securely) set it up on your Essentials server via the Anywhere Access / Remote Web Access set up wizard. Otherwise, you can get a free Let’s Encrypt SSL certificate using Certify the web instead (discussed below).
*NOTE: You may need to allow some time for your domain name to become fully propagated.
**NOTE: You can purchase a trusted SSL certificate from any certificate provider such as Namecheap, etc. Personally, I use Comodo PositiveSSL Certificates from K Software because they are reasonably priced, and I’ve been happily dealing with them for many years now.
To begin the domain name and trusted SSL certificate set up process in Anywhere Access / Remote Web Access:
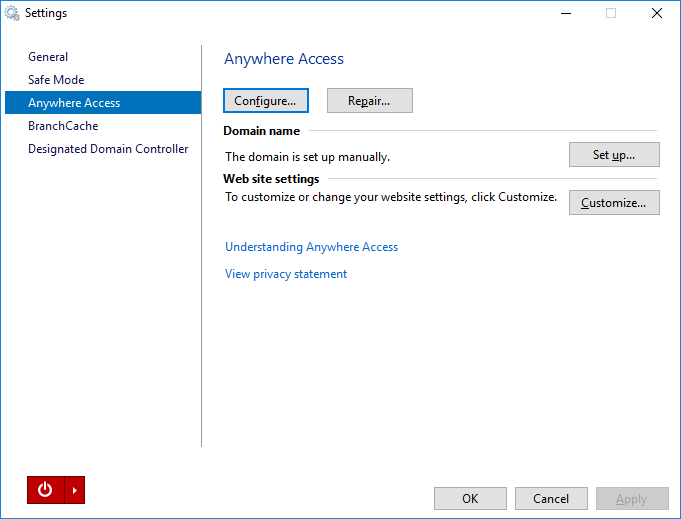
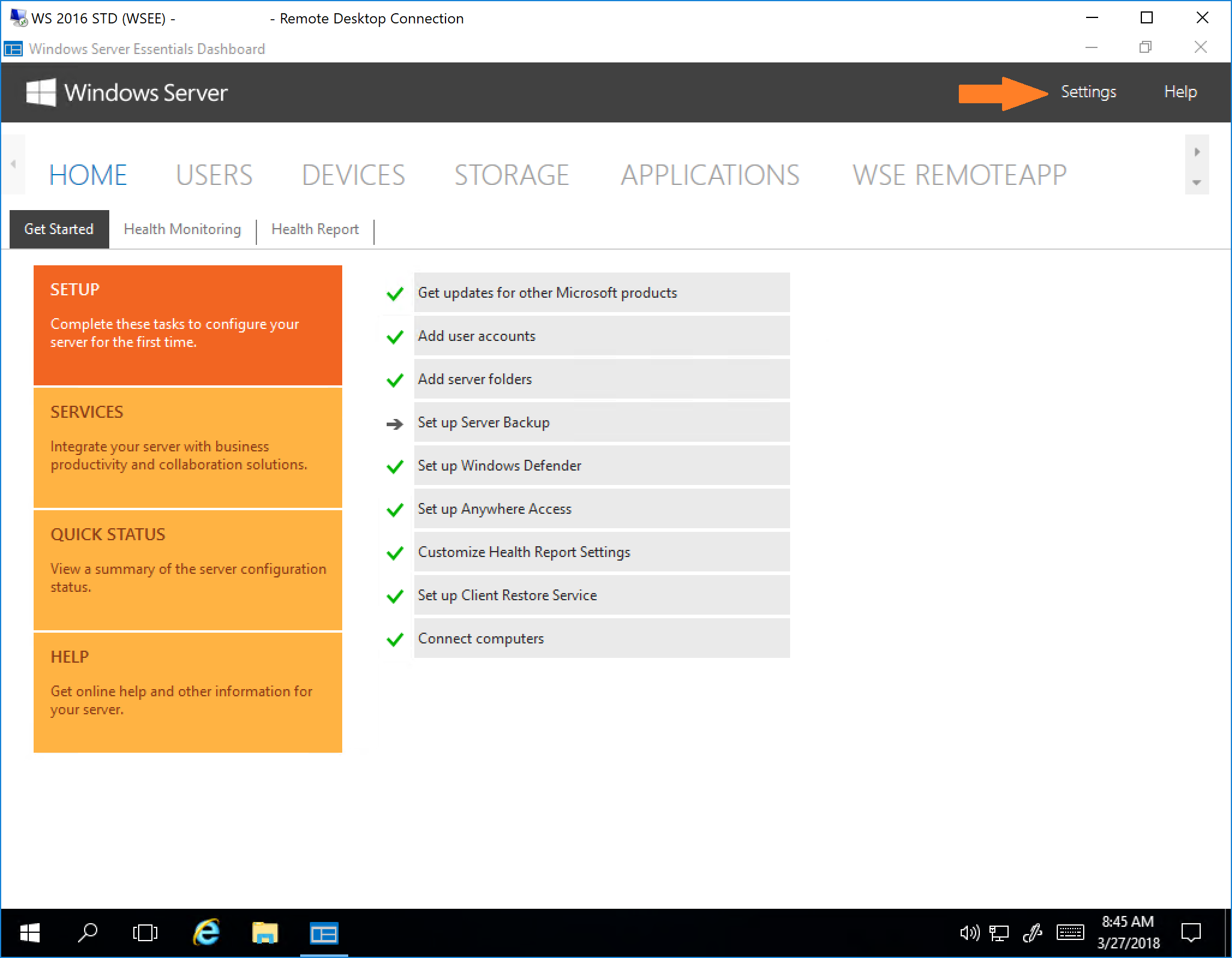
1. Start the Windows Server Essentials Dashboard and click “Settings“.
2. Click the “Anywhere Access” tab, and click “Configure“.
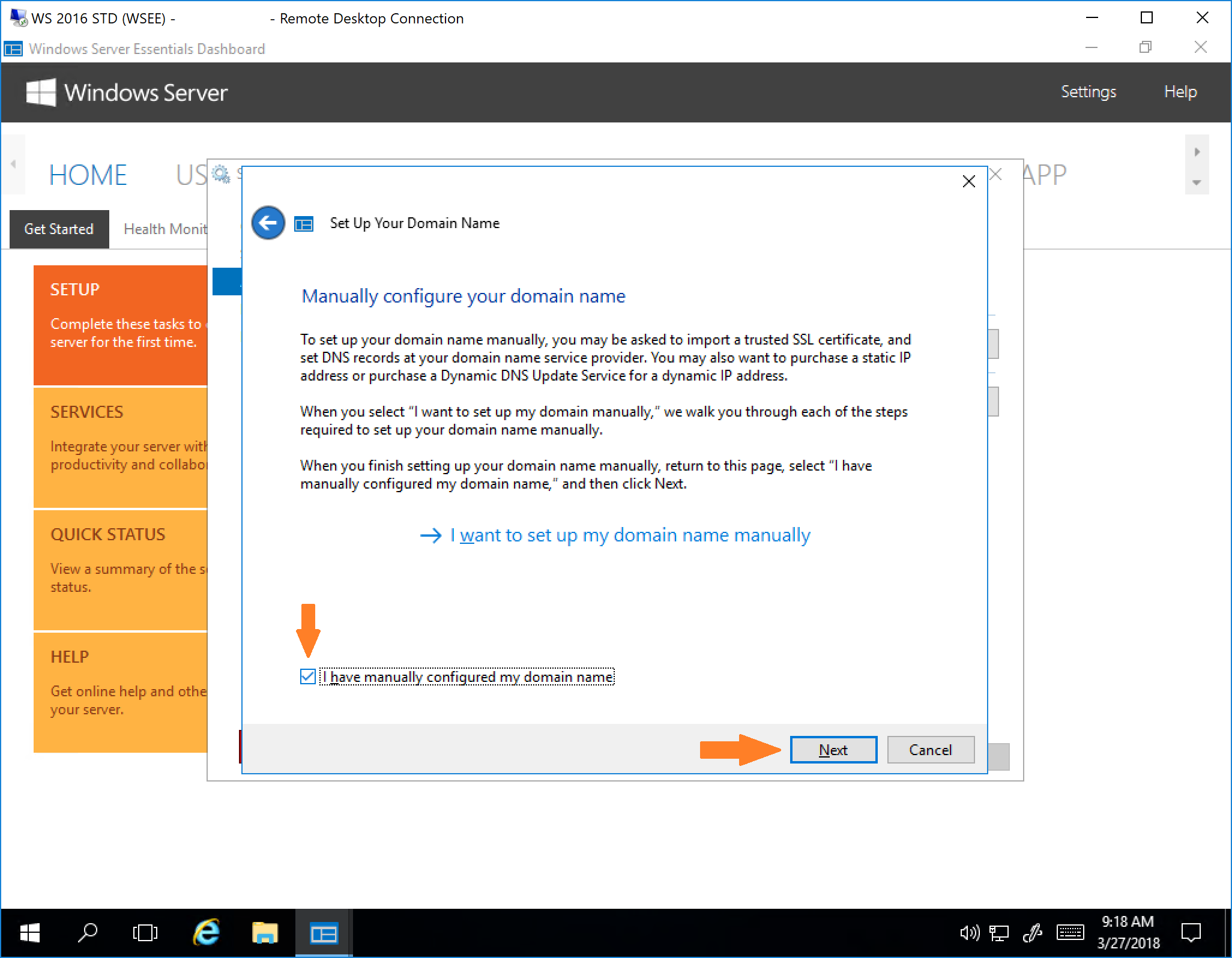
3. Click “Next“.
NOTE: If you already have a domain name configured (such as a Microsoft personalized domain name, etc.), be sure to uncheck the “Skip Domain Name setup. I have already set up my domain name.” checkbox, and then choose the “Use another domain name or domain name service provider” option shown in the Set Up Your Domain Name wizard that appears.
4. Choose the “I want to use a domain name I already own” option, enter your custom / vanity domain name (i.e. YourCustomDomain.com WITHOUT the leading YourDomainPrefix portion), and click “Next“.
NOTE: Essentials already includes support for a large number of TLDs (top level domain names), but if you happen to come across one that doesn’t work for you, then just let us know and we can add support for it on-the-fly (e.g. “.uk“, “.top“, etc.).
5. Since you have already purchased your domain name, set up a dynamic DNS update service, and set up your domain name prefix (subdomain) and public DNS records over at your domain name registrar in the previous sections of this tutorial, you can go ahead and check the “I have manually configured my domain name” checkbox here, and click “Next“.
6. Specify the domain name prefix you decided on (if you went with something other than the recommended “remote” prefix, then click “Change” to enter it), choose the “I want to purchase a trusted SSL certificate for the domain name” option, and click “Next“.
7. Click “Copy” to copy the provided encoded data to the clipboard, and paste it into the space provided on the SSL certificate request page of your certificate provider’s website (and click “Next when you are ready to continue).
8. Once you have received your trusted SSL certificate information as encoded data, or as a file, choose the “I have the trusted SSL certificate information from my certificate provider” option, and click “Next“.
NOTE: If you need more time, then choose the “My certificate provider needs more time to process the request” option, and run the wizard again at a later time so that you can import the certificate information.
9. Choose the “Copy and paste the encoded text from your trusted SSL certificate provider” option, and paste in your certificate’s encoded data.
NOTE: If your certificate provider gave you a certificate file instead, then choose the “Select the certificate file (*.cer) from your trusted SSL certificate provider” option, and click “Browse“. If you received a .crt file (as opposed to a .cer file) from your certificate provider, then just change the Open file dialog box’s file type drop-down list from “X.509 Certificate (*.cer)” to “All files (*.*)” so that you can see and select the .crt file.
10. Complete the remainder of the Anywhere Access / Remote Web Access set up wizard.
That’s it, you’re all finished! [Jump to the conclusion]
ALTERNATIVELY, you can get a free Let’s Encrypt SSL certificate using Certify the web as follows…
INFO: The free Let’s Encrypt SSL certificates expire every 90 days, and so without a reliable way to automatically renew them, they can be a real hassle for long time use with your Essentials server’s Anywhere Access / Remote Web Access feature. Fortunately, Certify the web takes care of doing the certificate renewals for you.
NOTE: While Certify the web can automatically renew the Let’s Encrypt SSL certificate for you, it unfortunately does not offer any (easy) way to “properly” configure the SSL certificate for use with an Essentials server. We might be able to muddle our way though all of the various deployment and scripting settings in Certify the web in order to have it configure the Let’s Encrypt SSL certificate renewals for your Essentials server, but I’m not going to try and do that here. Rather, with the target audience of this tutorial being our customers, I’m instead going to guide you through setting up Certify the web with a post-request PowerShell script* that will notify our products any time your Let’s Encrypt SSL certificate has been renewed. Our products will then identify the new certificate, and instruct the native tools built into Essentials to configure it properly for use with your Essentials server. This way you can rest assured that your renewed Let’s Encrypt SSL certificate will always be configured so that it works correctly with ALL of the Anywhere Access / Remote Web Access features of your Essentials server (no muss, no fuss!).
*INFO: The WSEE Installer Version 10.0.14393.4169 (Revision 26) or greater, WSE RemoteApp Version 1.255.1526.0 or greater, and/or WSE WorkFolders Version 1.0.67.0 or greater are required to use the script.
Get The Certificate
1. Download the latest version of Certify the web from here.
2. Start a Remote Desktop Connection to your Essentials server, sign in as an administrator, and then run the Certify the web setup file directly from the administrator’s desktop in order to install Certify the web on your Essentials server.
3. Start Certify the web, click “New Certificate“, and register a new contact when prompted to do so (so that you will be notified on any certificate renewal failures, etc.).
INFO: Doing this will also create a new Automated Certificate Management Environment (ACME) account (i.e. Certificate Authority account) for Let’s Encrypt in Certify the web, which is required in order for you to be able to successfully request certificates.
a) In the Edit ACME Account dialog box that appears, choose “Let’s Encrypt” as the Certificate Authority, type in your Email Address, check the “Yes, I Agree” checkbox, and click “Register Contact” to create a new Let’s Encrypt Certificate Authority account.
INFO: You can edit the newly created Let’s Encrypt Certificate Authority account (or create a new account) in Certify the web at any time by clicking on “Settings” and then “Certificate Authorities“.
4. On the “Certificate” tab that appears, select the “Default Web Site” website.
5. Type in the fully qualified domain name that you have decided on (e.g. remote.YourCustomDomain.com), and click the “Add Domains” (+) button.
NOTE: You can enter a wildcard domain here if desired (e.g. *.YourCustomDomain.com). However, non-wildcard fully qualified domains are recommend for most use cases (e.g. remote.YourCustomDomain.com).
6. Verify that the added domain name is correct, and that it will be the primary domain included in the certificate.
NOTE: If you have previously set up Anywhere Access / Remote Web Access on your Essentials server, then a hostname binding for your server’s name will already exist, and you will need to uncheck its “INCLUDE” checkbox so that it DOES NOT get included in the certificate (or, even better, you can just use the trashcan button in order to completely remove it from the list instead).
7. Click the “Advanced” sub-tab, and then under “Certificate Authority” select the “Let’s Encrypt” certificate authority.
8. Click the “Authorization” tab, and select the “dns-01” challenge type.
TIP: You can use the default “http-01” challenge type here if your ISP doesn’t block HTTP port 80 (which is required for http-01 domain validation), and if you are not using a wildcard domain (which requires dns-01 domain validation). Click the “Test” button to see if HTTP validation will work for you. If it succeeds, then proceed to step #12 below.
9. Select “acme-dns DNS API” as your DNS update method and click the “Test” button.
NOTE: The list of DNS API provider’s that are currently supported by Certify the web can be found here. Or, you may choose the “(Update DNS Manually)” option if you would prefer to manually create the required ‘TXT’ record in the DNS zone of your domain.
10. You will be prompted to create a ‘CNAME’ record pointing to the trusted acme-dns server. You can copy the required ‘CNAME’ record information to the clipboard by clicking on the text within the “Test Progress” pane.
INFO: Further instructions for setting up acme-dns can be found here.
11. Add a new “_acme-challenge” ‘CNAME’ record, via the DNS manager at your domain registrar or DNS provider, using the information that was provided to you within the “Test Progress” pane.
12. Click the “Deployment” tab, and select the “Certificate Store Only” deployment mode.
13. Click the “Tasks” tab (or “Deployment Tasks” sub-tab), and click the “Add” button that’s located under the Deployment Tasks section.
a) Scroll down the (long) list of available deployment tasks until you locate the “Run Powershell Script” deployment task, and click its “Select” button.
b) In the Edit Deployment Task dialog box that appears, type “[Post-Request Script]” into the Task Name field.
c) Click the “Task Parameters” sub-tab, type the full path to the “CertifyTheWebHelper.ps1” script file into the Program/Script field, and click “OK“.
NOTE: The CertifyTheWebHelper.ps1 script file will be located on the Essentials server within our software product’s “Scripts” folder (“C:\Program Files\The Office Maven\Essentials\Scripts“, “C:\Program Files\The Office Maven\WSE RemoteApp\Scripts“, or “C:\Program Files\The Office Maven\WSE WorkFolders\Scripts“).
IMPORTANT NOTE: While other websites suggest that you can simply use Certify the web‘s built-in RDGatewayServices.ps1 script here (by choosing the “Deploy to RDP Gateway Service” deployment task) in order to configure the Let’s Encrypt SSL certificate on an Essentials server (for its initial deployment and/or for configuring its auto renewal), I can 100% tell you that this is not enough seeing as the SSL certificate needs to be configured in multiple places within Essentials beyond in just IIS and the RDP Gateway Service. It is far better to allow the native tools that are built into Essentials to configure the SSL certificate properly for you, and the only way to ensure that happens correctly (outside of manually configuring/repairing Anywhere Access via the server Dashboard each time) is to let our products automatically instruct Essentials to do it for you through the use of our CertifyTheWebHelper.ps1 script.
INFO: The script simply writes the new SSL certificate’s thumbprint value to the registry, which alerts our software products that a new SSL certificate has been installed, and they then instruct Essentials to go ahead configure the new SSL certificate accordingly.
14. Click the “Preview” tab, review the summary information, and click “Test“.
15. When the test completes / succeeds, close the “Test Progress” pane, and click “Save“.
16. Click “Request Certificate“.
SUCCESS! You now have a free Let’s Encrypt SSL certificate in IIS for your custom / vanity domain name.
INFO: From the “Status” tab, you can see that Auto Renewal is enabled by default, and will automatically renew your free Let’s Encrypt SSL certificate as required (via Certify the web‘s “Certify SSL Manager Service” that is now running on your Essentials server).
NOTE: By default, Certify the web will automatically renew your certificate every 30 days (even though it’s actually valid for a full 90 days). This way, you will know well in advance if there happens to be a validation problem when renewing the certificate, allowing you plenty of time to rectify the problem before your certificate actually expires. If 30 days seems to be a bit on the cautious side for you, then you can increase it (up to 45, 50, or even 60 days) by clicking on “Settings“.
Export The Certificate
Next you will need to export your new Let’s Encrypt SSL certificate from IIS so that it can be set up in Anywhere Access / Remote Web Access:
1. From the administrator’s server desktop, right-click the Start button, click “Control Panel“, open “Administrative Tools“, open the “Internet Information Services (IIS) Manager” applet, click on your Essentials server’s name, and then double-click “Server Certificates“.
2. Select (highlight) your Let’s Encrypt SSL certificate, and click “Export“.
3. Save the Let’s Encrypt SSL certificate to the administrator’s server desktop (using any password of your choice).
Set Up The Certificate
Lastly, you will need to set up your exported Let’s Encrypt SSL certificate in Anywhere Access / Remote Web Access for your domain name as follows:
1. Start the Windows Server Essentials Dashboard and click “Settings“.
2. Click the “Anywhere Access” tab, and click “Configure“.
3. Click “Next“.
NOTE: If you already have a domain name configured (such as a Microsoft personalized domain name, etc.), be sure to uncheck the “Skip Domain Name setup. I have already set up my domain name.” checkbox, and then choose the “Use another domain name or domain name service provider” option shown in the Set Up Your Domain Name wizard that appears.
4. Choose the “I want to use a domain name I already own” option, enter your custom / vanity domain name (i.e. YourCustomDomain.com WITHOUT the leading YourDomainPrefix portion), and click “Next“.
NOTE: Essentials already includes support for a large number of TLDs (top level domain names), but if you happen to come across one that doesn’t work for you, then just let us know and we can add support for it on-the-fly (e.g. “.uk“, “.top“, etc.).
5. Since you have already purchased your domain name, set up a dynamic DNS update service, and set up your domain name prefix (subdomain) and public DNS records over at your domain name registrar in the previous sections of this tutorial, you can go ahead and check the “I have manually configured my domain name” checkbox here, and click “Next“.
6. Specify the domain name prefix you decided on (if you went with something other than the recommended “remote” prefix, then click “Change” to enter it), choose the “I want to use an existing SSL certificate” option, and click “Next“.
7. Import the Let’s Encrypt SSL certificate you that you just saved to the administrator’s server desktop (using your chosen password).
8. Complete the remainder of the Anywhere Access / Remote Web Access set up wizard.
That’s it, you’re all finished!
Conclusion
You will know that you are all set up correctly when, from a computer outside of your network, you type NSLOOKUP YourDomainPrefix.YourDomainName.com into a command prompt and it returns the public (WAN) IP address of your network router (i.e. the one your ISP gives you), and that when you browse to https://YourDomainPrefix.YourDomainName.com/remote, that you don’t get a certificate warning when the Essentials server’s built-in Remote Web Access sign in page comes up. Doing this ensures that you have both HTTPS port 443 forwarded correctly in your router, and that the trusted SSL certificate is installed correctly.
That’s all there is to it! Enjoy using your custom / vanity domain name with your Essentials server.
— MIKE (The Office Maven)
SOURCES:
How to Manually Configure SBS 2011 Essentials Internet Domain Name
Use a new or existing domain name
Dynamic DNS and domain hosted with GoDaddy (DuckDNS solution)

 Posted by Mike
Posted by Mike 
 Last updated: December 7, 2025
Last updated: December 7, 2025