Enabling TLS 1.2 On Windows Server Essentials
The latest release of WSE RemoteApp (Version 1.255.1836.0 or greater) now allows you to enable TLS 1.2 on Windows Server Essentials, while disabling TLS 1.0 and TLS 1.1, in order to enhance the security of SSL connections made with the server, and to comply with the latest compliance standards for the Federal Risk and Authorization Management Program (FedRAMP). It has long been thought that TLS 1.0 could not be disabled on an Essentials server since it is required for client-to-server communications (such as client computer backups, connecting client computers to the server via http://<YourServerName>/connect, etc.). However, it has recently been brought to my attention that this actually can be achieved when specific .NET Framework security settings are added to both the server and to ALL of your client computers. With TLS 1.2 enabled, and TLS 1.0 and TLS 1.1 disabled, you will be able to obtain an A+ grade (as of this writing), from the SSL Labs SSL Server Test site for your Essentials server’s built-in Remote Web Access websites.
How To Setup IIS for SSL Perfect Forward Secrecy and TLS 1.2
To setup Internet Information Services (IIS) for SSL perfect forward secrecy and TLS 1.2, open the server Dashboard application, go to the main “WSE REMOTEAPP” page, and click the “Remote Desktop Session Settings” task located in the “Users Tasks” pane.

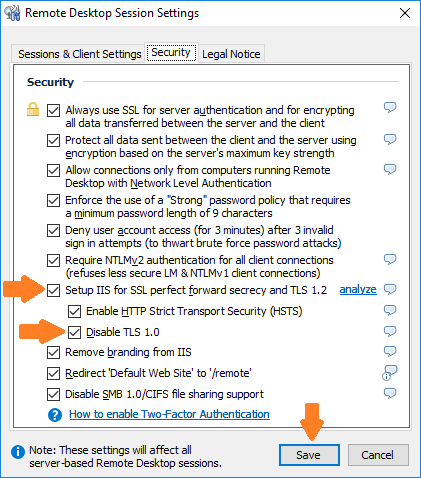
In the “Remote Desktop Session Settings” dialog box that opens, click on the “Security” tab, check the “Setup IIS for SSL perfect forward secrecy and TLS 1.2” checkbox, and then check the “Disable TLS 1.0” checkbox.
💡 TIP: You should also check the “Enable HTTP Strict Transport Security (HSTS)” checkbox to protect the server’s Remote Web Access website against protocol downgrade attacks and cookie hijacking. Enabling HSTS is also required in order to obtain an A+ grade.
Read the information shown on the dialog box that opens, and then check the “I understand and want to disable TLS 1.0” checkbox. Next, click on the “Download .REG File…” button, and save the provided DotNetFrameworkTlsSettings.reg file. After doing that, click on the “OK” button.

Back on the “Remote Desktop Session Settings” dialog box, click the “Save” button in order to save your changes, and then restart the server when you are prompted to do so.
You will then need to run the provided DotNetFrameworkTlsSettings.reg file, that you’ve just downloaded, on ALL of your client computers and restart them!
❗ IMPORTANT: If you disable TLS 1.0 on the server, then you MUST add the required .NET Framework security settings to ALL of your client computers (by simply running the provided DotNetFrameworkTlsSettings.reg file on, and then restarting, them) in order for them to be able to successfully connect to, and communicate with, the server. This includes all client computers that you intend to connect to the server via http://<YourServerName>/connect (otherwise the Windows Server Essentials Connector software’s wizard will not be able to discover the server!).
Lastly, click the “analyze” link on the “Security” tab of the “Remote Desktop Session Settings” task to test the new SSL configuration of your server’s built-in Remote Web Access website (or you can head over to the SSL Labs SSL Server Test site and manually type in your server’s RWA address).
Questions & Answers (Q&A)
• Can TLS 1.3 be used instead of TLS 1.2?
TLS 1.3 is enabled by default under Windows Server 2022 and greater, and so it will be used (in lieu of TLS 1.2) under those operating systems when using the latest release of WSE RemoteApp (i.e. Version 1.255.1852.0 or greater).
EDIT (1/5/2021): In addition to enabling TLS 1.3, Microsoft has also added support for disabling legacy TLS (e.g. TLS 1.0/1.1, weak cipher suites, etc.) on select SSL certificate bindings from within Internet Information Services (IIS) under Windows Server 2022 and greater:
This new feature gives us the ability to disable legacy TLS on the Essentials server’s Anywhere Access / Remote Web Access websites, while still leaving it enabled on the server for the other Windows Server Essentials components to use. Basically, instead of disabling TLS 1.0 throughout entire server, we can now selectively disable it on only the Anywhere Access / Remote Web Access websites (eliminating the issues Windows Server Essentials runs into when TLS 1.0 has been disabled on the entire server).
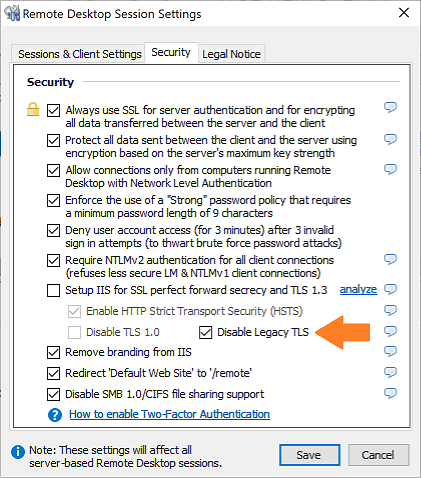
However, there’s an oddity (bug?) in Windows Server Essentials that prevents us from using the new “Disable Legacy TLS” feature in IIS… If you attempt to manually edit any of the bindings for the Essentials server’s Anywhere Access / Remote Web Access websites in IIS, it messes up the binding information for the website, and in the case of the “Default Web Site“, it causes a health alert to appear in the Essentials server’s Dashboard stating that “Remote Desktop Services is not configured correctly“. When the error is repaired, the “Disable Legacy TLS” functionality is automatically removed from the website. In order to workaround this issue/bug, a new “Disable Legacy TLS” checkbox has been added to the “Security” tab of the “Remote Desktop Sessions Settings” task in the latest release of WSE RemoteApp (i.e. Version 1.255.1882.0 or greater):
Checking this checkbox will disable legacy TLS on all of the Essentials server’s Anywhere Access / Remote Web Access websites (i.e. Default Web Site, Mac Web Service, WSS Certificate Web Service, and SSTP VPN) without you needing to manually edit all of the bindings within IIS and hence triggering the above mentioned issue/bug.
• Can this be done without having WSE RemoteApp installed on my Essentials server?
It sure can be if you’re willing to put in the effort. To get started see:
Setup Microsoft Windows or IIS for SSL Perfect Forward Secrecy and TLS 1.2
Transport Layer Security (TLS) best practices with the .NET Framework
Conclusion
That’s it! I hope everyone enjoys being able to enable TLS 1.2 on their Essentials servers via WSE RemoteApp. I look forward to hearing your feedback on this new feature (and as always, both positive and negative feedback is more than welcome).
— MIKE (The Office Maven)

 Posted by Mike
Posted by Mike 
 Last updated: January 3, 2024
Last updated: January 3, 2024